I gave myself a resolution this year that I'm gonna write more posts but I've been busy because of the exam period. Fortunately, everything went smoothly and I managed to get myself a two-week break before the summer semester starts.
This blog will be about reverse engineering and the course I attended in the winter semester. It pretty much met my expectations. The course was lectured and tutored by Ing. Josef Kokeš. At first, I was confused and even sometimes disgusted by the amount of assembly code we had to look through but as the time passes, I got used to it. This process was mainly to be able to orientate what is happening in the code. Well, at least roughly.
During the course we used a lot of tools but the one I'd like to mention is IDA Freeware.
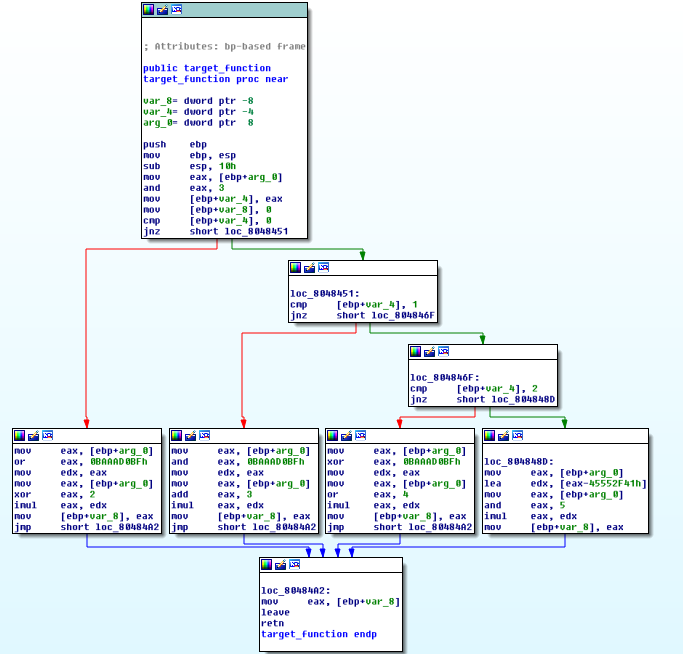
It showed the code flow of the program, meaningly how the program is structured and it helps to focus on the part we are trying to understand. Well this was easy to get used to. The worst part was when we tried to deobfuscate the code. With the deobfuscations, the IDA (at least the free version) couldn't parse it into the graphical code flow thanks to the injecting the dead code and using a method called opaque predicates. For this we had to manually mark and change the data/code management of IDA to show it properly.
Although, we used only the basic techniques so deobfuscation was not such a big deal. However, when the code was wrapped, it became a pain to find the entry point of the program and dump the code (or at least for me) for the static inspection, otherwise it wouldn't showed up.
The task that I enjoyed the most was hooking up the IAT (Import Address Table) and re-routing the existing functions to one of our own. Basically, one must find the address of the IAT and afterwards the address of the structures IMAGE_IMPORT_DESCRIPTOR which contains the name of the function and the address that is initialized when starting the program. The task we had was to create a custom "memory management" which only logged the allocations.
An example of the code, getting the IAT:
HMODULE hPEFile = GetModuleHandle(NULL); // NULL znamená aktuální
PIMAGE_DOS_HEADER pDosHeader = (PIMAGE_DOS_HEADER)hPEFile;
*base = (BYTE*)pDosHeader;
PIMAGE_NT_HEADERS pNTHeaders = (PIMAGE_NT_HEADERS)(*base +pDosHeader->e_lfanew);
*start = (IMAGE_IMPORT_DESCRIPTOR*) (*base + pNTHeaders->OptionalHeader.DataDirectory[1].VirtualAddress);
*end = (IMAGE_IMPORT_DESCRIPTOR*) ((BYTE *)*start + pNTHeaders->OptionalHeader.DataDirectory[1].Size);To summarize my experience with reverse engineering, I learned a lot but if I had to do this fulltime I would go crazy since most of the tasks took me way too long to solve. For example, the task where we had to find the password which was encoded with RC4. Reading RC4 encoding in the assembly wasn't such fun.